Identity Governance Automation: How to Implement AI-Powered IGA
Discover how to implement AI-powered identity governance automation to streamline access control, reduce risk, and ensure compliance. Learn key features and implementation steps for your enterprise.
Table of Contents
Identity is the new security perimeter, and managing who has access to what has never been more complex. With hundreds of SaaS apps, hybrid infrastructures, and a growing number of non-human identities, traditional Identity Governance and Administration (IGA) systems are under pressure. Manual provisioning, ticket-based workflows, and static access reviews can no longer keep up with the speed of business or the scale of risk.
Enter identity governance automation: the next evolution in IGA. By leveraging AI and automation, organizations can move beyond reactive compliance to implement proactive, policy-driven access control. Automated IGA streamlines user lifecycle management, continuously monitors risk, and enforces least-privilege access at scale; without bottlenecking IT or security teams.
This article explores what identity governance automation is, why it matters, and how to implement AI-powered IGA in your organization.
What Is Identity Governance Automation?
Identity Governance Automation is the process of applying automated policy enforcement, risk scoring, and lifecycle orchestration to user and machine identities to ensure appropriate access controls. By analyzing usage patterns and compliance requirements, AI-powered IGA platforms identify excessive privileges, enforce segregation of duties, and trigger automated provisioning or deprovisioning. For example, when an employee moves departments, the system revokes outdated entitlements and requests approvals for new roles without human intervention. This continuous, intelligence-driven mechanism enhances security, reduces audit penalties, and accelerates onboarding.
This definition sets the stage for understanding why legacy solutions fail to keep pace with modern identity demands.
Why Legacy IGA Falls Short
Legacy IGA platforms were built for a different era – one where IT environments were smaller, static, and largely on-premises. Today’s organizations, however, are navigating sprawling SaaS ecosystems, hybrid cloud infrastructure, and a rapid increase in non-human identities such as service accounts and bots.
As a result, traditional IGA systems struggle to keep pace. Manual reviews and provisioning create bottlenecks and introduce human error, while limited integration with modern tools leaves critical systems unmanaged. Without real-time policy enforcement or comprehensive visibility, especially into machine identities, security gaps widen and compliance becomes harder to maintain.
Below, we explore the key limitations of legacy IGA and why a modern, automated approach is now essential.
- Manual Reviews and High Operational Overhead
- Incomplete Integration with Modern SaaS and Cloud Apps
- Lack of Real-time Policy Enforcement
- Poor Visibility Into Machine and Non-human Identities
Manual Reviews and High Operational Overhead
Traditional IGA requires periodic human-led access certifications that consume countless hours. Reviewers often rely on outdated spreadsheets to validate entitlements, resulting in delayed remediations and audit backlogs. These manual cycles hinder quick response to internal risk changes.
Transitioning to automated access reviews reduces overhead and ensures immediate policy adherence.
Incomplete Integration with Modern SaaS and Cloud Apps
Many legacy platforms integrate poorly with cloud-native applications and microservices, creating unmanaged identity silos. Without full API connectivity, enterprises lack visibility into user and service-to-service communications. Expanding connectors and applying AI-driven discovery closes these gaps and unifies governance across all resource types.
Lack of Real-time Policy Enforcement
Rule-based engines enforce policies on schedules rather than continuously, allowing privilege creep between review cycles. Real-time enforcement powered by risk scoring and anomaly detection prevents unauthorized access at the moment it occurs. This proactive posture minimizes exposure windows.
Poor Visibility Into Machine and Non-human Identities
Automated credential issuance and API keys for bots, containers, and service accounts often slip outside governance processes. Without machine-identity insights, organizations struggle to monitor privileged scripts or automated processes. AI-enabled IGA catalogs these non-human entities, applies adaptive controls, and alerts teams to suspicious automation patterns.
These challenges underscore the need for AI-powered identity governance capable of continuous, integrated, and intelligent controls.
Core Capabilities of AI-Powered IGA Platforms
AI-powered IGA platforms represent a significant leap forward from traditional, manual systems. By leveraging artificial intelligence and automation, these next-gen platforms streamline identity processes, reduce human error, and improve security at scale.
Rather than relying on ticket-based workflows and reactive audits, AI-driven IGA continuously monitors access, enforces policies in real time, and learns from user behavior to refine permissions dynamically. From automating provisioning and access requests to simplifying reviews and enforcing separation of duties (SoD) policies, these platforms are designed to support both compliance and agility.
Automated Provisioning & Access Requests
Modern IGA platforms equipped with AI and automation capabilities are transforming how organizations handle provisioning and access requests. Traditionally, provisioning access required manual ticketing, approval chains, and IT intervention – often resulting in delays, inconsistent access decisions, and significant administrative overhead.
Automated provisioning enables self-service access where employees can request the resources they need through a unified portal. Intelligent policy engines evaluate each request in real time, automatically approving or escalating based on predefined access policies, user roles, and risk context. For example, a marketing employee requesting access to campaign analytics tools may receive instant approval if their role and attributes align with policy parameters – no IT bottlenecks required.
This automation not only improves user productivity by dramatically reducing wait times, but also enhances security and compliance by enforcing consistent rules. AI further enhances the system by learning from historical approvals, flagging anomalies, and optimizing decision-making over time.
For IT and security teams, this means fewer tickets, greater control, and a scalable way to provision access across hundreds of SaaS apps and systems – supporting least-privilege access from day one.
Automated Access Reviews & Certifications
Access reviews and entitlement certifications are critical for meeting compliance requirements like SOX, HIPAA, and ISO 27001; but they’re notoriously manual, time-consuming, and error-prone when done with legacy systems. AI-powered IGA platforms change the game by making these processes faster, smarter, and more effective.
With automated access reviews, the platform continuously monitors user entitlements and usage patterns to proactively identify excess or unnecessary access. During scheduled certifications, AI assists reviewers – typically managers or application owners – by recommending which entitlements to revoke, based on inactivity, role misalignment, or potential violations of segregation of duties (SoD) policies.
For example, if a user has access to both finance systems and approval workflows, the system can flag this as a risk and prompt reviewers to investigate or revoke one of the permissions. These AI-suggested cleanups reduce "rubber-stamping" and help ensure that only the right users retain the right access at the right time.
Simultaneously, the platform automatically captures and organizes audit-ready evidence, including timestamps, reviewer decisions, and policy justifications. This drastically reduces the compliance burden on security teams and ensures full traceability for internal and external audits.
The result? A streamlined, intelligent approach to access governance that improves security posture, minimizes audit fatigue, and ensures continuous compliance.
Risk Enforcement & SoD Controls
Effective identity governance isn’t just about granting access – it’s about controlling risk. One of the most critical components of this is enforcing Segregation of Duties (SoD) and applying real-time risk detection across the identity lifecycle. AI-powered IGA platforms elevate these capabilities with continuous monitoring, dynamic policy enforcement, and intelligent alerting.
Traditional IGA solutions often rely on static rules and delayed batch processes, which can miss violations until it's too late. In contrast, modern platforms use real-time controls to detect and block policy violations as they happen. For instance, if a user attempts to request access that would allow them to both initiate and approve financial transactions, an SoD violation, the system can automatically flag or block the request, or reroute it for enhanced scrutiny.
These platforms continuously evaluate user access against organizational policies, risk scores, and SoD matrices, making it easier to prevent toxic permission combinations and reduce insider threat exposure. AI can also prioritize violations by risk level, helping security and compliance teams focus on what matters most.
By preventing excessive access before it’s granted and maintaining a continuous watch for risky entitlements, AI-powered SoD enforcement becomes a proactive shield against fraud, error, and compliance violations – without slowing down the business.
Policy-Based Access Management
Modern identity governance demands a shift from static role assignments to dynamic, context-aware access policies. With AI-powered IGA platforms, organizations can implement policy-based access management that aligns tightly with Zero Trust principles; minimizing standing privileges while maximizing agility and control.
Instead of pre-assigning broad entitlements that remain active indefinitely, policy-based models enable “just-in-time” access – granting users access to specific systems or data only when needed, for a defined period, and under controlled conditions. This not only reduces the attack surface but also supports least-privilege access across all identities, including contractors, vendors, and service accounts.
Advanced platforms can define access policies using a blend of attributes such as user role, department, geography, risk score, and time of access. For example, a developer requesting access to production systems may be required to justify the request, trigger elevated approval workflows, or receive access only during a maintenance window.
Automated expiration ensures that temporary access is revoked automatically, removing the burden from IT and closing one of the most common gaps in traditional access management – lingering permissions.
By combining AI with policy-based authorization, organizations can enforce fine-grained controls, adapt to changing contexts in real time, and operationalize Zero Trust without slowing productivity.
AI in Identity Governance: Capabilities and Advantages
Artificial Intelligence is rapidly transforming Identity Governance and Administration from a manual, reactive process into an intelligent, proactive system. By embedding AI into core identity functions, organizations gain the ability to scale governance, reduce risk, and make smarter decisions faster. Below are four critical ways AI enhances identity governance; and why these capabilities are game changers for modern IT and security teams.
- Identity Analytics and Risk Scoring
- AI-Driven Risk Scoring and Policy Enforcement
- Autonomous Policy Management
- Automated Testing and Validation
Identity Analytics and Risk Scoring
AI enables identity analytics at scale by continuously ingesting and analyzing data across users, roles, applications, and entitlements. This includes behavioral patterns, login activity, access requests, and anomalies across cloud and on-prem environments. With this context, AI can generate real-time risk scores for every identity, whether human or machine, enabling organizations to focus their efforts where the risk is highest.
For example, a user with excessive entitlements who begins accessing high-risk systems outside of normal working hours may be flagged automatically for further review. This approach replaces static entitlement models with dynamic, risk-informed identity monitoring, significantly improving accuracy and audit readiness.
{{shadowbox}}
AI-Driven Risk Scoring and Policy Enforcement
AI not only identifies risky behaviors but can enforce policy decisions in real time. By comparing current access and behavior against defined risk thresholds and historical baselines, AI-driven IGA systems can automatically trigger workflows, such as revoking access, escalating for review, or adjusting user roles.
This capability supports Segregation of Duties (SoD) controls and compliance enforcement without relying on manual interventions. Policies become adaptive – responding to shifting risk conditions and business changes instantly, without waiting for a periodic audit or review.
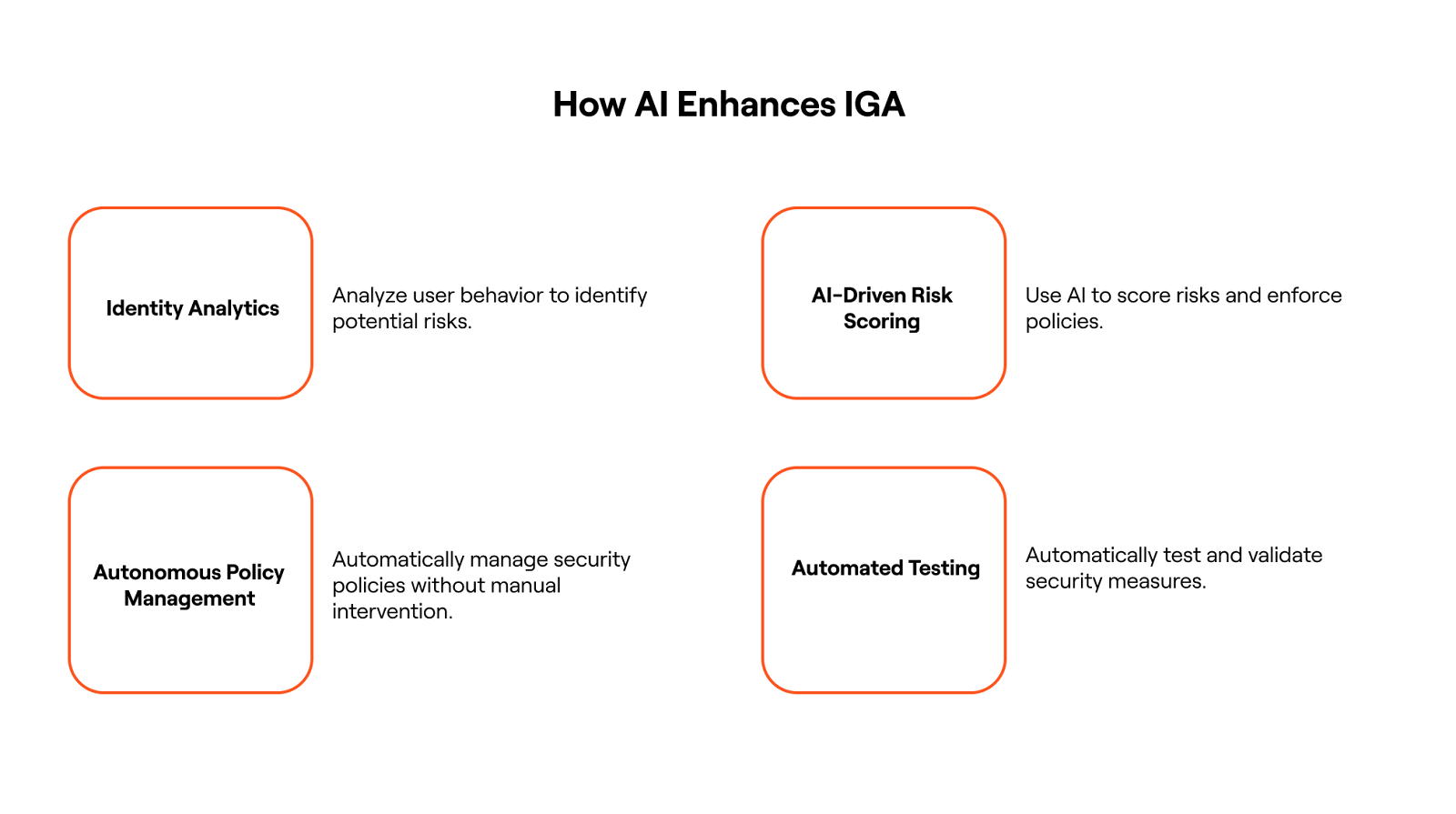
Autonomous Policy Management
One of the most impactful use cases of AI in IGA is autonomous policy management. Traditional access policies require constant upkeep from IT and security teams, leading to policy drift, over-permissioning, and compliance gaps. With AI, organizations can automatically generate, maintain, and refine policies based on real-world access patterns, business context, and user behavior.
For instance, if a specific team consistently accesses a defined group of applications, AI can recommend a new policy grouping those entitlements together – streamlining future provisioning. Over time, the platform evolves and hardens policy structures while minimizing human effort and the risk of misconfiguration.
Automated Testing and Validation
AI also plays a critical role in automated access validation. Through intelligent testing, AI can simulate user access scenarios, detect misconfigurations, and identify policy violations before they become vulnerabilities. These tests can be run continuously or triggered by changes in user roles, system configurations, or policy updates.
This results in audit-ready evidence collection, fewer false positives, and faster remediation times. Automated validation ensures that policy intent matches actual system behavior, keeping compliance efforts aligned with real-world operations.
By embracing AI across these domains, organizations can achieve more than just efficient identity governance; they can implement autonomous, intelligent, and resilient IGA strategies that scale with the business and adapt to modern threats.
Key Features of Modern IGA Platforms
As identity and access management grows more complex – with hybrid environments, thousands of SaaS apps, and an explosion of machine identities – traditional IGA platforms have struggled to keep up. Modern IGA solutions are built to meet today’s demands with automation, intelligence, and user-centric design. Below are three foundational features that define next-generation IGA platforms and enable security and IT teams to govern access at scale.
- Comprehensive Integration Support
- Unified Identity Maps
- Scalability & Time to Value
Comprehensive Integration Support
The average enterprise now manages more than 650 applications, spanning cloud, on-prem, and hybrid environments. Legacy IGA platforms often cover only a fraction of these, leaving blind spots and unmanaged access behind.
Modern IGA tools offer broad, out-of-the-box integration support for cloud services (e.g., AWS, Microsoft 365, Salesforce), developer tools (e.g., GitHub, Jira), HRIS systems (e.g., Workday, BambooHR), and identity providers (e.g., Okta, Azure AD). This connectivity is essential for enabling automated provisioning, access reviews, and real-time enforcement across the full application landscape.
In addition, leading platforms provide extensible APIs and integration frameworks, allowing security teams to build and maintain custom connectors for niche or proprietary systems. This ensures full coverage and governance across the long tail of apps that often go overlooked.
Unified Identity Maps
As users interact with multiple systems and assume different roles over time, their identity can become fragmented across directories, apps, and environments. This creates challenges for governance, auditing, and access management.
Modern IGA platforms solve this with unified identity maps – a centralized model that reconciles all user accounts, entitlements, and roles across systems into a single source of truth. This enables IT and security teams to:
- Understand the full scope of each user’s access
- Detect anomalies like duplicate accounts or privilege sprawl
- Perform accurate access reviews and certifications
- Enforce least-privilege access policies across all identities
Unified identity mapping is particularly critical for managing non-human identities (e.g., service accounts, bots, machine users), which often lack clear ownership and present high risk.
Scalability & Time to Value
A common pitfall of legacy IGA deployments is long implementation cycles, often measured in months or years, before realizing value. Modern platforms prioritize fast time to value, offering pre-built templates, automated policy generation, and AI-powered recommendations that accelerate onboarding and outcomes.
Scalability is also key. As organizations grow, merge, or evolve their infrastructure, their IGA solution must keep pace. Next-gen platforms are built to scale horizontally, handle increasing volumes of identities and access requests, and adapt to new regulatory requirements with minimal overhead.
By combining speed, scale, and automation, modern IGA solutions transform identity governance from a check-the-box function into a strategic enabler of security, compliance, and operational efficiency.
These core capabilities are what differentiate modern IGA platforms from their predecessors; and why forward-thinking IT and security teams are making the shift now.
Steps to Implement IGA Automation
Successfully implementing IGA automation isn’t about flipping a switch – it requires a methodical rollout rooted in strategic planning and smart execution. These five key steps offer a blueprint for IT and security teams to evolve from manual identity processes to streamlined, AI-driven governance.
- Assessment & Planning – Map existing processes, identify gaps, and define success metrics.
- Tool Selection & Integration – Evaluate AI‑driven platforms that align with your app ecosystem.
- Policy Definition & Risk Controls – Begin with core policies and simulate with AI.
- Automate Reviews & Lifecycle Workflows – Deploy self-service access, certifications, and mover/leaver automation.
- Monitor, Test, and Improve – Leverage dashboards, analytics, and continuous testing to evolve your approach.
1. Assessment & Planning
Start by auditing your current identity governance practices. Identify pain points like inconsistent access provisioning, excessive manual reviews, or delayed offboarding. Map out the systems, roles, and processes that touch identity – from HR and IT to security and compliance. This phase is also the time to define key success metrics: time-to-provision, access request volumes, audit pass rates, and privilege creep reduction are strong indicators to track.
Collaborate cross-functionally during this step. Ensure stakeholders across compliance, security, and business units are aligned on automation goals and risk tolerance. The assessment phase provides the foundation for every downstream decision.
2. Tool Selection & Integration
Choose an IGA platform that aligns with your needs today – and scales with your future. Look for tools that offer broad integration capabilities with your existing tech stack: HRIS, ITSM, directory services, and cloud/SaaS applications. AI maturity matters here – prioritize platforms with embedded analytics, automation, and explainability.
Once selected, begin phased integration. Start with core systems and high-risk apps, then expand to lower-priority systems over time. Ensure your IGA solution can ingest, normalize, and contextualize identity data across environments to enable automation.
3. Policy Definition & Risk Controls
Effective IGA automation requires clear, enforceable policies. Define role-based and attribute-based access policies (RBAC and ABAC), map them to business responsibilities, and integrate them into your workflows. Implement Segregation of Duties (SoD) controls to prevent risky entitlement combinations and apply risk scoring to prioritize enforcement.
AI tools can support policy creation by analyzing historical entitlement usage and surfacing common patterns. Automating this discovery can reduce policy drift and tighten enforcement without overburdening security teams.
4. Automate Reviews & Lifecycle Workflows
Automate recurring tasks that historically bog down IT and compliance teams. Start with access certifications: AI-powered reviews can flag outliers, recommend removals, and collect audit-ready evidence. Apply the same automation to joiner-mover-leaver (JML) processes – automatically provisioning access on day one, updating entitlements during role changes, and revoking permissions upon departure.
By embedding automation into these workflows, you accelerate operations, reduce human error, and minimize exposure time for excessive access.
5. Monitor, Test, and Improve
IGA automation isn’t “set it and forget it.” Ongoing monitoring and iterative testing are essential to ensure policies remain effective and automation continues to align with business needs. Use dashboards, alerts, and user behavior analytics (UBA) to detect anomalies and measure policy adherence.
Test regularly: simulate role changes, run mock audits, and validate AI recommendations against human decisions. The best programs use these insights to tune policies, improve ML models, and drive continuous governance improvement.
Trends Driving IGA Innovation
Identity Governance and Administration has rapidly evolved from a static compliance requirement into a dynamic, business-critical function. Modern IGA is no longer just about who has access – it’s about how access is granted, monitored, and removed in real-time across increasingly complex environments. Below are four emerging trends that are driving the next wave of IGA innovation for IT and security leaders.
- Non-Human Identity Governance – Managing service accounts, containers, and machine credentials with the same rigor as user identities helps close automation blind spots and prevent supply-chain attacks.
- Real-Time Access Control – Dynamic policy evaluation at the time of access request eliminates windows of opportunity for misuse.
- Zero Standing Privilege – Just-in-time provisioning grants elevated rights only for the duration needed, reducing persistent attack surfaces.
- Data Privacy and Compliance Alignment – Automated tagging of personally identifiable information (PII) and policy enforcement ensures continuous adherence to GDPR, CCPA, HIPAA, and other regulations.
Non-Human Identity Governance
The rise of automation, APIs, and DevOps practices has exploded the number of non-human identities in enterprise environments. Service accounts, bots, cloud functions, and machine-to-machine (M2M) credentials now far outnumber human users.
Legacy IGA tools were never designed to handle this complexity. Today’s platforms must extend governance beyond users to include automated processes and workloads. This means tracking entitlement usage for bots, enforcing least-privilege access for service accounts, and setting expiration policies on non-human credentials. Without visibility and control over these identities, organizations face major blind spots in their security posture.
Real-Time Access Control
Static, role-based access models can’t keep up with the pace of modern business. Employees often need immediate, temporary access to systems or data – especially in dynamic environments like DevOps, customer support, or incident response. Delays in provisioning slow down productivity and open the door to over-permissioning when temporary access becomes permanent.
Real-time access control is emerging as a foundational IGA capability. This includes “just-in-time” provisioning, where users are granted access for a limited period based on contextual triggers or approval workflows. By integrating identity context, risk scoring, and dynamic policy enforcement, modern IGA platforms enable secure, time-bound access without manual bottlenecks.
Zero Standing Privilege
Zero Standing Privilege (ZSP) is a natural extension of the Zero Trust philosophy. Instead of granting long-term access to sensitive systems, ZSP ensures that privileges are only elevated when needed; and are immediately revoked afterward. This eliminates persistent, high-risk entitlements that attackers often exploit in lateral movement and privilege escalation attacks.
Modern IGA platforms are incorporating ZSP by embedding policy-based access approvals, automatic privilege revocation, and activity logging. When combined with session monitoring, these capabilities offer fine-grained control over who can access what – and when – with full auditability.
Data Privacy and Compliance Alignment
With the growing web of global regulations like GDPR, HIPAA, and CCPA, data privacy is no longer a separate function from identity governance – it’s intertwined. Access decisions now carry significant legal and financial implications. IGA must not only enforce who has access to personal data, but also ensure that data handling aligns with consent and purpose limitations.
Innovative IGA solutions are bridging identity governance and data privacy by tagging sensitive data, mapping it to user entitlements, and automating compliance reporting. AI-driven tools can detect anomalies, automate access reviews, and even flag compliance risks – making privacy enforcement both scalable and actionable.
How Lumos Powers Autonomous Identity Governance
Modern identity governance is undergoing a radical transformation. As organizations grow more distributed and adopt more cloud applications, legacy IGA systems – built for static environments – struggle to scale. Manual access reviews, role sprawl, and siloed systems increase risk while slowing down the business.
AI-powered IGA changes the equation. With automated provisioning, continuous access reviews, and intelligent policy enforcement, enterprises can reduce operational overhead, tighten security, and improve audit readiness. When done right, IGA is no longer a checkbox; it becomes a driver of efficiency, compliance, and agility.
Lumos takes identity governance to the next level with the industry's first truly autonomous identity platform. Designed to unify access across SaaS, cloud, and on-prem environments, Lumos delivers complete lifecycle automation, granular visibility, and AI-powered intelligence to scale governance without the manual burden.
- Albus AI, Lumos' agentic AI, automates role discovery, access policy creation, and entitlement cleanup—ensuring least privilege at scale.
- Lifecycle Automation manages joiners, movers, and leavers without the gaps that create security risks.
- Unified Access Visibility across every app – legacy or modern – ensures no shadow access goes unnoticed.
- Built-in compliance support with centralized audit trails and automated reviews helps teams stay always ready for audits.
With Lumos, organizations shift from reactive governance to proactive, autonomous identity security – built for the demands of today’s enterprise.
Ready to modernize your IGA strategy? Book a demo with Lumos today and take the first step toward a more secure, efficient future.
Mitigate security risks with Lumos: Minimize the blast radius of potential breaches and prevent unauthorized access, ensuring that users only have the exact permissions they need, when they need them. Book a demo now to learn more.




