Defeating The APPocalypse: The Autonomous Identity Revolution
This paper outlines why legacy approaches fail and introduces Autonomous Identity as the necessary evolution.

.avif)
Enterprises face a critical identity crisis, the "APPocalypse," driven by an explosion of applications and diverse identities (human, bot, AI), often with non-human identities outnumbering human ones 50:1. Traditional Identity Governance & Administration (IGA) tools cannot cope, creating critical security risks, operational drag, significant financial waste, and high total cost of ownership (TCO).
This is why Autonomous Identity is a necessary evolution of IGA solutions. Autonomous Identity uses AI to power complete visibility, actionable insights, full-cycle automation, and adaptive systems within identity governance. This transforms identity from a burden into a strategic advantage, securing the business, boosting productivity, and freeing teams for higher-impact work while increasing profitability through greater efficiency and lower TCO.
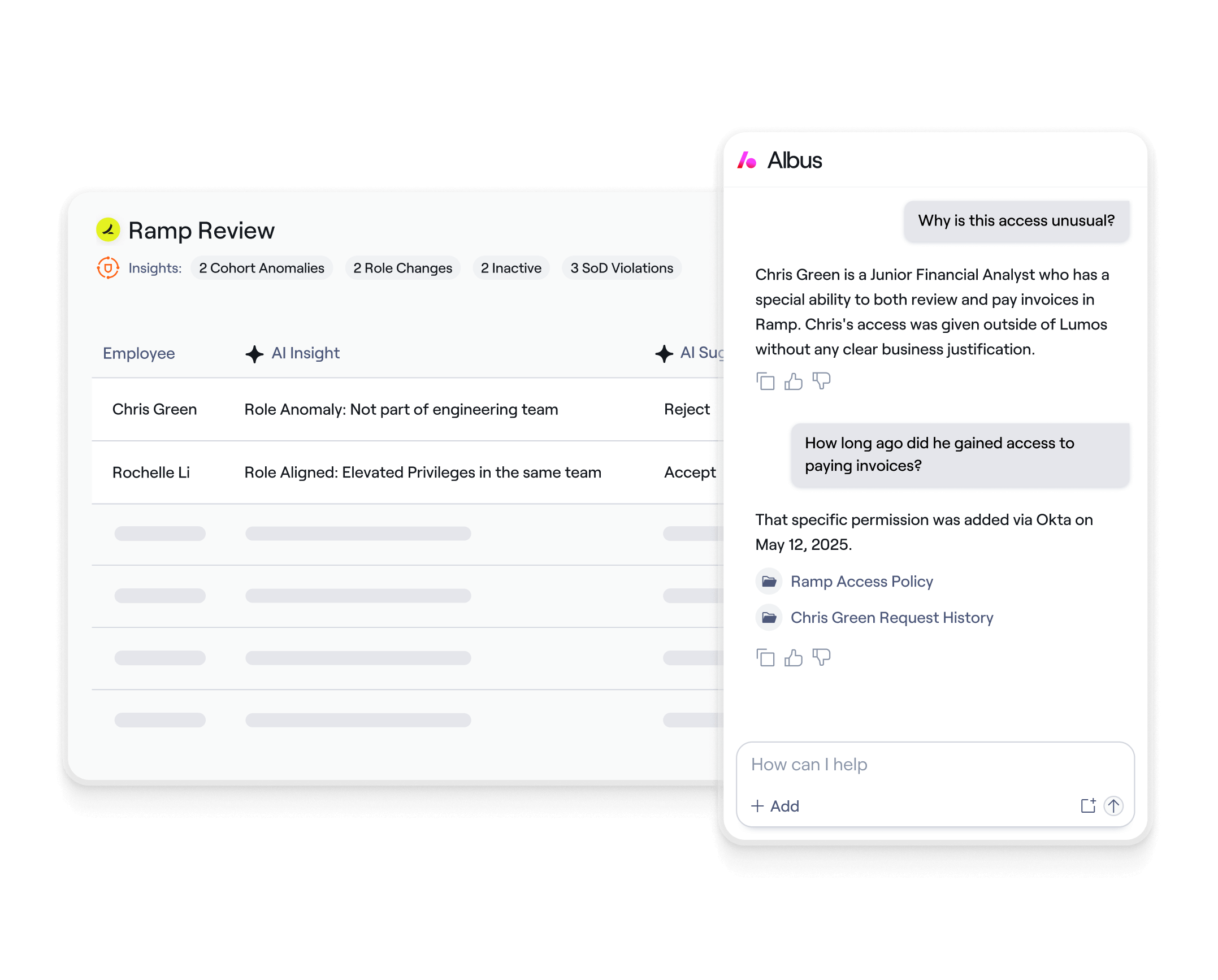
Today's Identity Governance is Broken
Traditional IGA wasn't built for today's reality, leaving you struggling with:
- Visibility Gaps: IGA tools cover only a fraction of apps, which take years to implement.
- Access Sprawl: Over time, users accumulate excessive access privileges that are not monitored.
- Click Fatigue: Essential workflows remain manual and fragmented.
- Static Systems: Rules and policies become outdated quickly and don't keep up.

Autonomous Identity: The New Way
Identity teams are supposed to enable employees and manage risks, but the explosion of apps and identities has overwhelmed them with manual processes and busywork. With Autonomous Identity, they can delegate repetitive tasks and shift the balance back towards strategic initiatives.
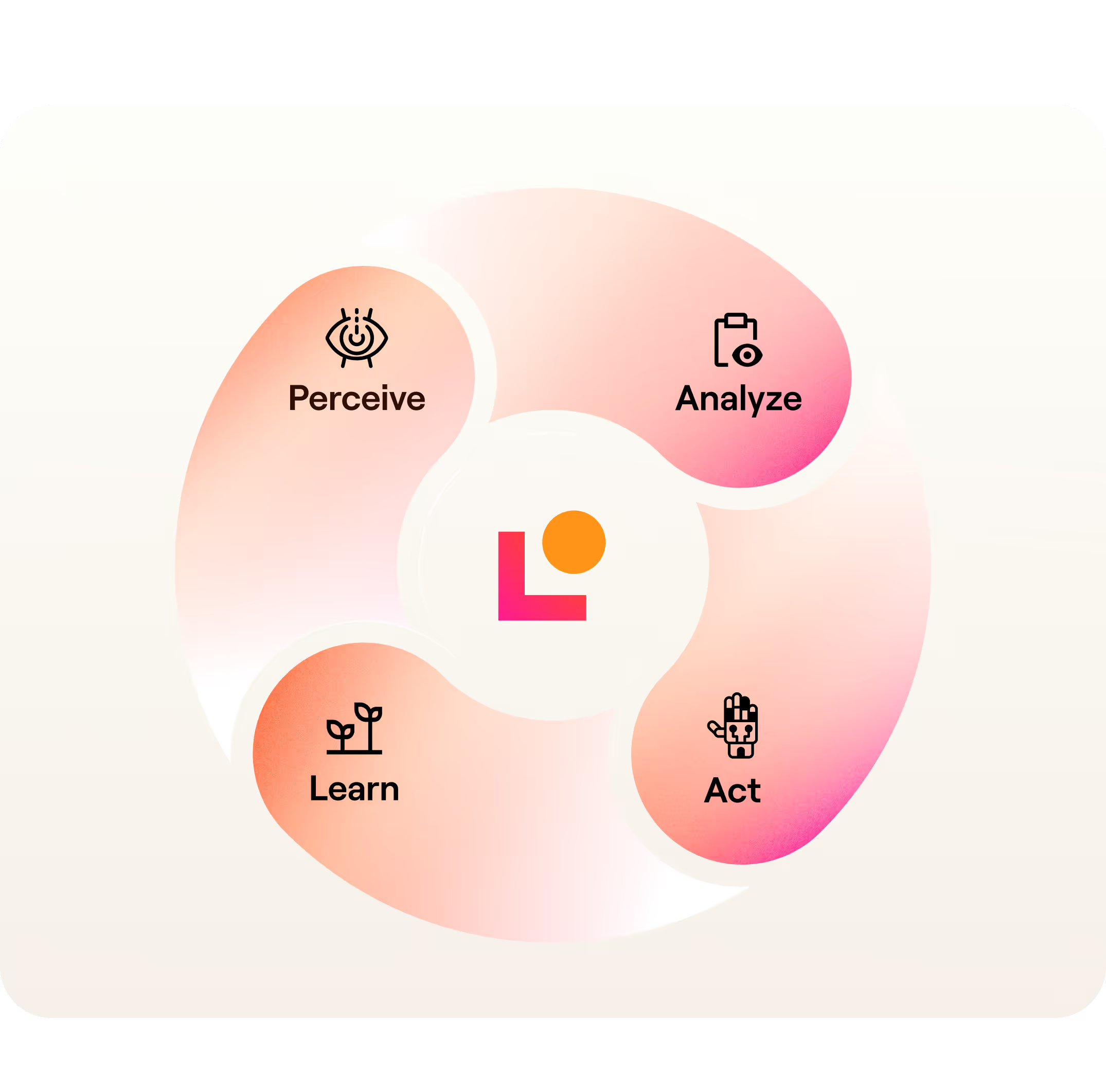
The Identity Framework
How do we get there? By building four key capabilities:
- Perceive: Eliminate blind spots with unified, real-time visibility of identities and entitlements.
- Analyze: Get actionable insights that detect anomalies, inefficiencies, and overspending.
- Act: Automate identity tasks—slash IT tickets up to 40%.
- Learn: Stay secure with adaptive, real-time access policies aligned with business needs.
The Benefits of Autonomous Identity
Autonomy isn’t instantaneous—it’s a strategic journey. Lumos delivers fast time-to-value by moving you from complex legacy processes to efficient Autonomous Identity. Lumos helps you achieve:
“Hackers don’t break in anymore. They log in. That’s why enforcing least-privilege is so critical. Lumos helps us automate policy creation and lifecycle management, so we can stay ahead of threats, simplify user access reviews, and make joiner-mover-leaver workflows run on autopilot. It’s a big step forward for security and the business.”
Achieve Complete Visibility with Lumos Autonomous Identity
Autonomous identity delivers comprehensive, real-time visibility. It automatically discovers and maps every app, identity (human, non-human, and even AI agents), permission, and associated activity data across cloud and on-prem apps. Lumos achieves this through universal connectivity, which includes the largest library of out-of-the-box SaaS integrations, flexible frameworks for custom connectors to APIs, directory services, and databases, and support for data capture from legacy systems.

Deliver Actionable Insights Through Lumos Autonomous Identity
Data overload isn't helpful; clear direction is. Autonomous identity employs analytics to provide actionable insights on the permissions carrying the most cost or risk. These insights pinpoint security threats like Separation of Duties (SoD) violations, excessive admin rights, unused permissions, access creep, or outlier access compared to peers.

Enable Full-Cycle Automation with Lumos Autonomous Identity
Manual changes cause friction and delays. Automate the entire identity lifecycle for all identity types with autonomous identity to drastically reduce IT admin overhead. Intelligent workflows also minimize standing privileges and secure sensitive resources to move organizations away from risky 'forever access.'

Build Adaptive Systems with Lumos Autonomous Identity
Static rules inevitably fall behind. Autonomous Identity enables true self-healing identity governance, creating an adaptive governance system using AI to continuously analyze behavior, usage patterns, and peer group activity.

Download the whitepaper to learn more
.avif)
Autonomous Identity FAQs
While environments differ, customers typically connect critical applications and begin seeing tangible results (like improved visibility into unused licenses or risky permissions) relatively quickly. Full deployment across hundreds of apps can often be achieved in months, not years.
Security is paramount. Lumos employs industry best practices including encryption at rest/in transit, achieves SOC2 Type II and ISO 27001 certifications, undergoes regular penetration testing, and adheres to strict data privacy regulations (GDPR, CCPA). We operate on a zero trust architecture.
ROI is based on quantifiable metrics including direct cost savings (reduced software spend, license optimization), operational efficiencies (reduced IT helpdesk load, faster audits/onboarding), and risk reduction (mitigating potential breach costs). We provide a customized ROI model based on your specific environment during the assessment phase.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.



