How to Implement Role-Based Security
Learn the benefits of RBAC implementation, including the role of principles like least privilege, separation of duties, and data abstraction.

Table of Contents
Role-based access control, or RBAC, has become increasingly important for companies across a wide range of industries. As the number of software applications used by the average organization continues to grow, the importance of well-defined security measures—including RBAC—grows as well.
By implementing the right RBAC solution and adhering to best practices for role-based access control implementation, companies can reduce their software spend without sacrificing productivity or security. This article will explore the benefits of role-based access control and how to implement an RBAC model that works for your organization, introducing some RBAC implementation best practices and keys to success along the way.
Why Is Role-Based Access Control Important?
With every new software application or resource an organization adopts, their overall software spend—and their need for effective access controls and permissions—increases.
In all too many companies, the growing number of software subscriptions becomes difficult to manage effectively, one of the key reasons why role-based access control is important. In response, many of these organizations choose the proverbial “path of least resistance” by granting broad access. Known as over-provisioning, this approach introduces its own problems in the form of unnecessary security vulnerabilities and increased software costs (based on licenses that aren’t even needed).
RBAC, by contrast, takes a more systemic approach to determining which members of a given organization need access to certain resources and preventing unauthorized access. There are three key “rules” behind an RBAC system, which inform how roles are defined and permissions are authorized.
How Do You Set Appropriate Role-Based Access Controls?

Setting up effective RBAC controls requires an understanding of three key principles or rules:
- Least Privilege: Determining the minimum level of access each user or role needs, on a role-by-role and asset-by-asset basis.
- Separation of Duties: Implementing compliance policies that restrict internal controls, preventing unauthorized access or misuse.
- Data Abstraction: Keeping the details of configured permissions hidden, and therefore more difficult to exploit.
Once you understand these three rules and how they function, the process of RBAC implementation becomes much more straightforward and focused.
How Is Role-Based Access Control Implemented?
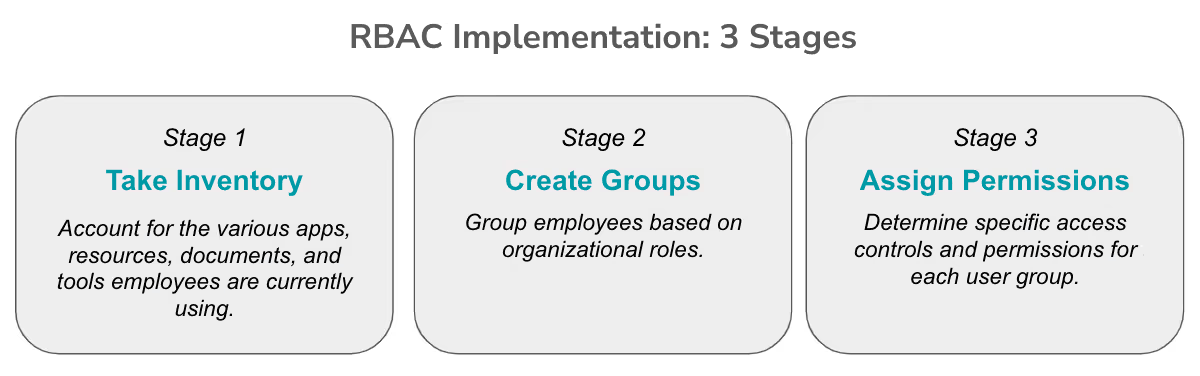
The process of implementing RBAC involves three key stages:
- First, you’ll need to take inventory of the various apps, resources, documents, and tools employees are currently using. As you create a comprehensive list, be on the lookout for software subscriptions that are either unused or unneeded, as you can reduce IT costs and increase security by discontinuing those contracts.
- Next, you’ll want to group employees based on organizational roles. This is a much more efficient process than setting permissions for each individual employee and application. When users are appropriately grouped, it also becomes much easier to monitor and manage access over time.
- Finally, you’re ready to determine specific access controls and permissions for each user group. As you work through this process, you may need to revisit how you’ve grouped employees. For example, you might initially group users by department, but then realize that different access levels are needed within those department-based groups (managers, for example, often require more permissions than their direct reports).
To recap:
The companies with the most effective RBAC systems are often those that understand that RBAC implementation isn’t a one-time activity. Instead, it’s something that needs to be monitored and adjusted as strategies and objectives shift over time. They also realize that effective RBAC implementation through purely manual processes is unnecessarily tedious, time-consuming, and ineffective. This underscores the importance of leveraging the right technology for the job—RBAC solutions, in other words.
What Are the Best Role-Based Access Control Tools?
The best RBAC tools are comprehensive RBAC solutions like Lumos, which empowers system administrators with the insights and tools they need to configure and implement an effective RBAC framework. The Lumos platform brings together a powerful set of features organizations can use to…
- Streamline workflows for creating user groups, defining roles, and determining the most appropriate RBAC models.
- Automate onboarding and offboarding processes for employees, getting them up to speed quickly.
- Reduce Costs by identifying and addressing unused and unneeded subscriptions.
- Increase security through the application of rules like the principle of least privilege and separation of duties, to minimize the risk of unauthorized or fraudulent access.
- Relieve IT teams by freeing them from the mountain of tickets by providing employees with self-service access request functionality.
Discover More
If you’re ready to learn more about how the Lumos platform works—or what an effective role-based access control implementation could look like for your organization, reach out to our team to book a demo.




