The Autonomous Identity Platform
Who has access to what, and should they? Lumos is the industry’s first autonomous identity platform to ensure the right users have the right access for the right time.

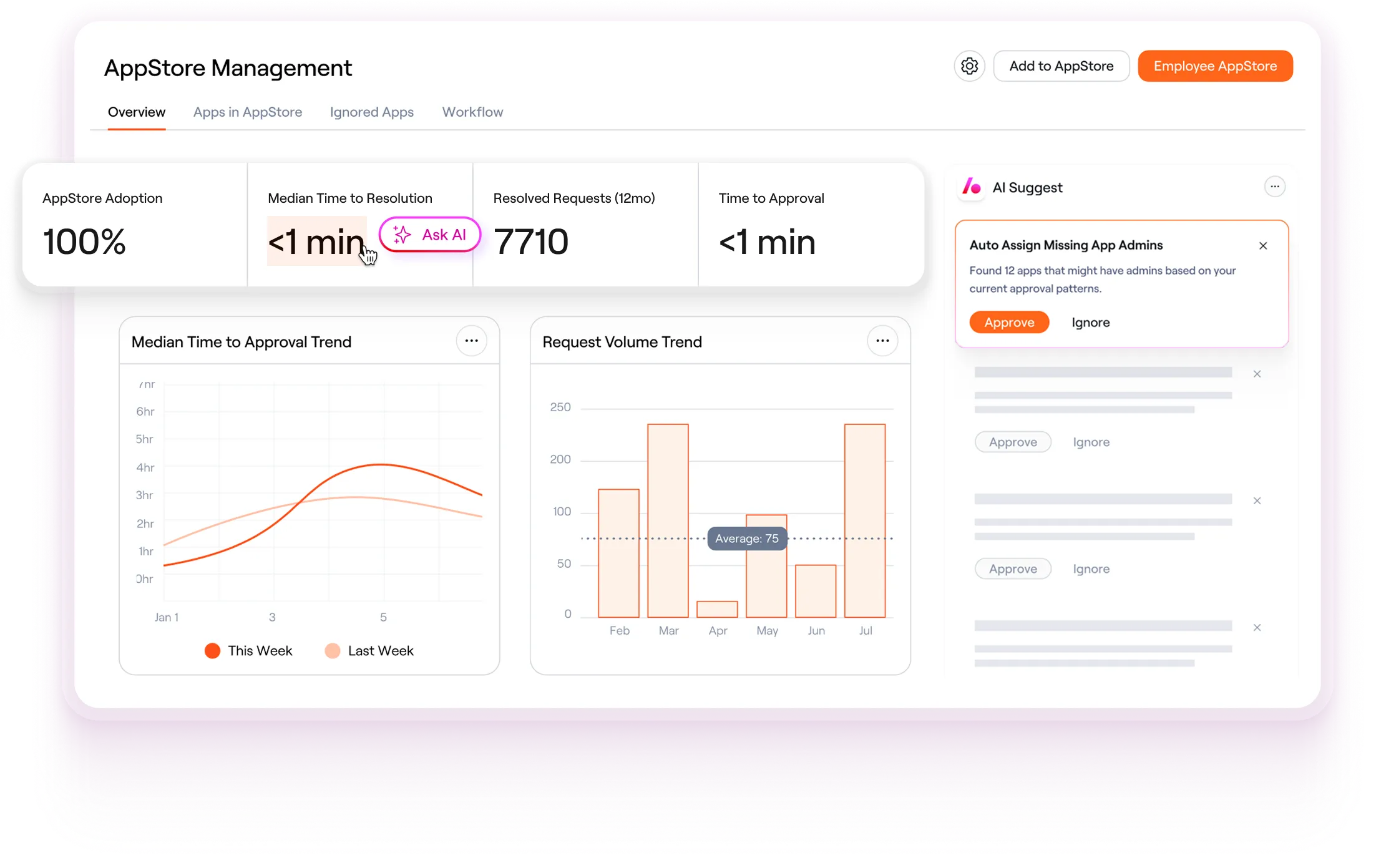







Even with modern identity governance tools, most organizations struggle to keep access under control. Expand your stack with the Lumos Identity AI Agent — no rip and replace required — or start with our end-to-end AI-Native Identity Governance Platform.
Bring Autonomy to IGA with Albus
Tame the complexity of identity with an agentic approach.
Explore Albus
AI-powered Role Mining
Albus ingests HRIS data, app assignments, and usage logs. It unearths common patterns and creates clean RBAC/ABAC policies. No more rubber-stamping.

Agentic Access Reviews
Albus approves or rejects using peer group analysis and usage anomalies. Admins and app owners oversee agent's decisions. Complete reviews in minutes, not days.

LLM-based Identity Analyst
Ask Albus queries in natural language — like, “Who has anomalous access in Snowflake?” It scans users, apps, and entitlements to flag dormant accounts, policy drift, and SoD violations. Uncover 10x more risks.
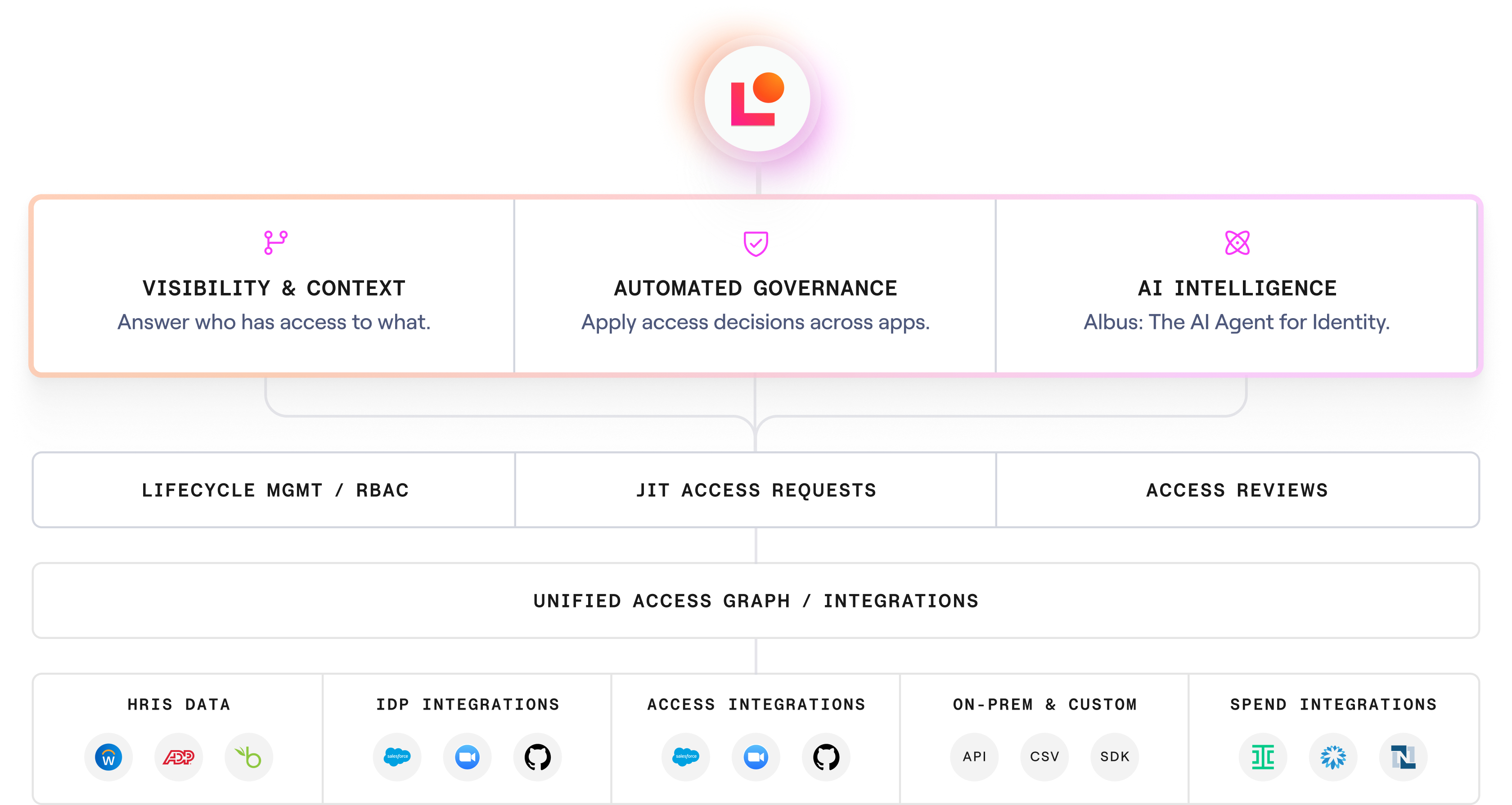
The First Autonomous Identity Platform
One platform for access reviews, self-service access, and joiner-mover-leaver workflows. Fast setup with AI-generated connectors, on-prem agent, SDK and webhooks.
Modular Products for Smarter Identity Governance
Everything you need to meet your modern IGA needs.
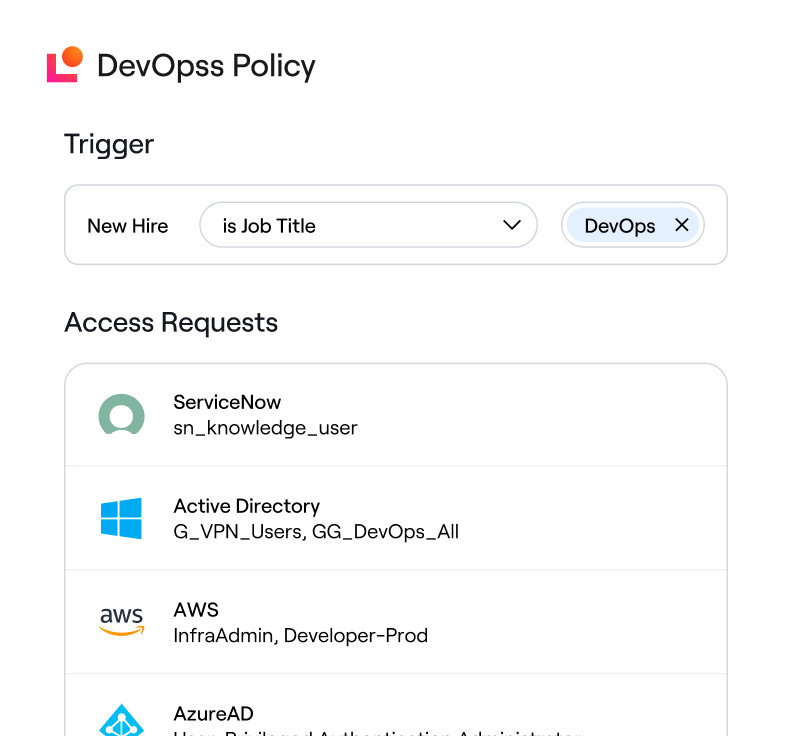
Role Mining
Mine roles and build RBAC/ABAC policies.

Lifecycle Management
Automate joiner-mover-leaver workflows.
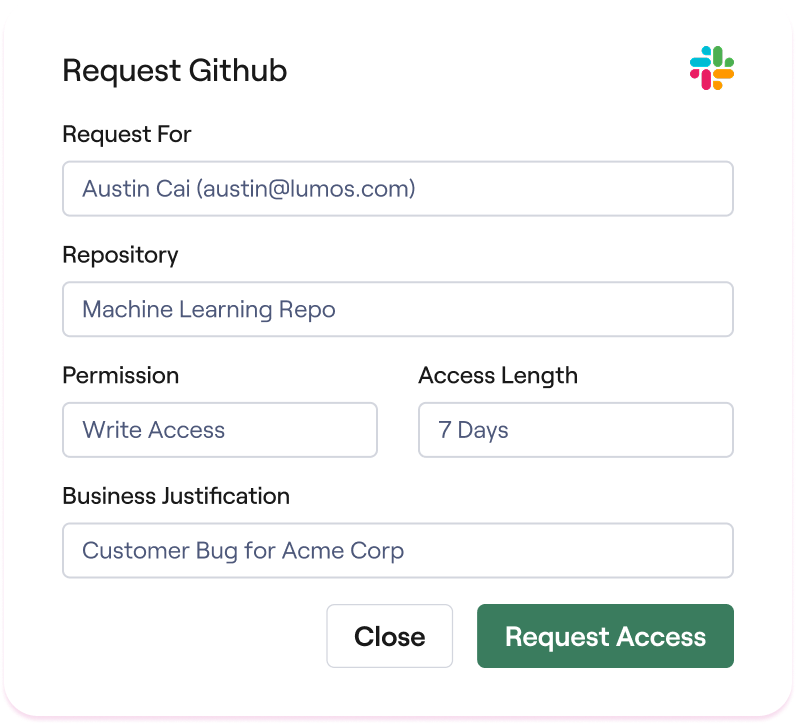
Access Requests
Enforce just-in-time access with self-service experience.
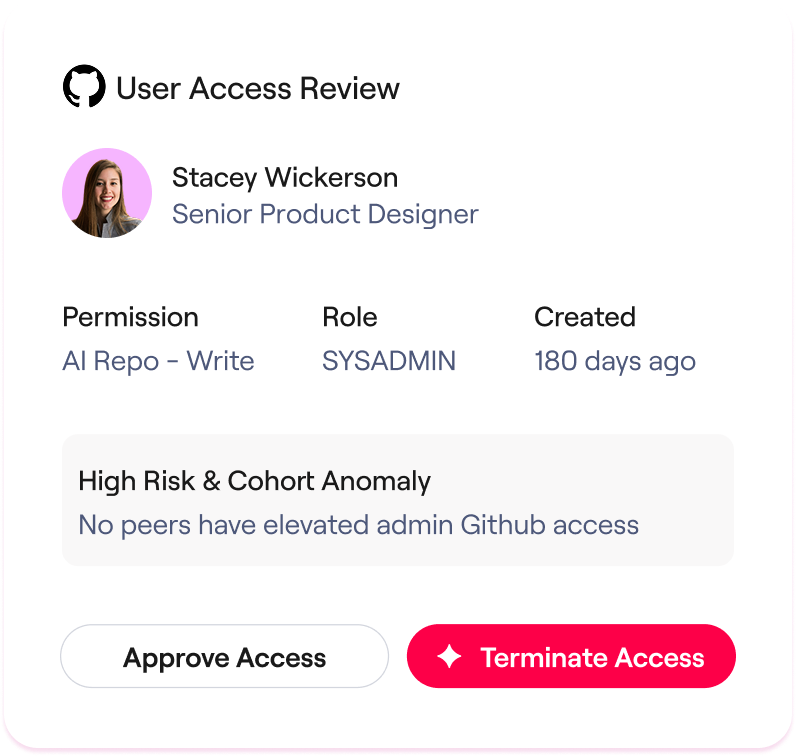
Access Reviews
Simplify certifications and audits with reporting and remediation.
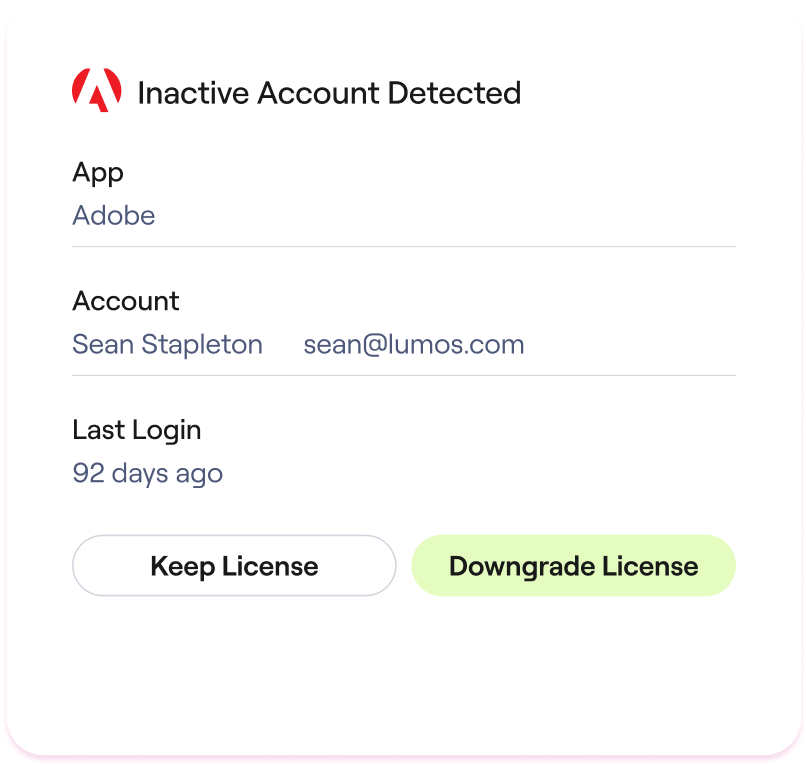
SaaS Management
Analyze SaaS usage versus spend and optimize licenses.

Identity Analytics
Customize dashboards and reporting for posture analysis.
“70% of organizations admit to excess access, and nearly half struggle to enforce least privilege effectively. Lumos’ “Autonomous Identity Platform” stands out by merging AI-generated policy management with lifecycle automation.”
Hear from Our Customers





“With Lumos, our access request ticket dropped by 72%, allowing us to automatically grant employees the access they needed and revoke them in record time.”
Senior Manager, Corporate IT, Prosper Marketplace

“Lumos helps us stay ahead of threats by automating policy creation and lifecycle management. It’s a big step forward for security and the business.”
Deputy Chief Information Security Officer, Mars




Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.



